VPNBook – How to download the Port 53 Certificate (Needs Winzip)
OpenVPN uses 2 files, that are critical. The first is the config file, the second is the security certificate.
Step 1 – Find the certificate link on VPNBook. Use the OpenVPN tab – UDP Port 53. Left Click once on this link.
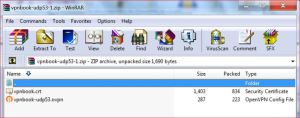
Step 2 – Winzip will launch – “Opening vpnbook-udp53.zip”
If you don’t have Winzip installed, you can find a free CNET version here:
http://download.cnet.com/WinZip/3000-2250_4-10003164.html
Step 3 – Winzip finds 2 files to extract. Click the Wizard Icon (7th Icon across).
Step 4 – Extract the 2 files on to your desktop (so that you can find them easily).
- The Wizard will open 2 files.
- Click on each file, right click and copy it.
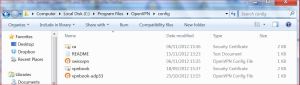
Step 5 – Use windows explorer. Start > Computer > C drive > Program Files > OpenVPN > config
Now paste the file here.
Repeat for the second file.
It’s important that BOTH files are pasted inside this directory.
Your c:\Program Files\OpenVPN\config will look something like this:
That’s it.
- This certificate stage only has to be done once for each VPN provider.
- However, if you swap from Port 53 to say Port 443, then you’d need to download a second certificate. (See the earlier links, you’ll see the Port 443 is listed too).
Have fun.
This stage is only done once. Phew!
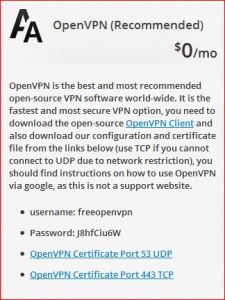
Your OpenVPN username and password are:





Cannot find the link for the Port 53
LikeLike
Hi Dirk,
1. http://www.vpnbook.com
2. OpenVPN tab.
3. Under this tab, look for “Certificate – UDP Port 53” link.
Click on this link, and it will start to download the file for you.
You’ll need winzip installed to open the file, and get the certificate and config files.
I hope that helps.
LikeLike
I am in the Netherlands and getting a 404 on vpnbook
VPN was working fine for me until today.
I want to go to OpenVPN.
Are we blocked in the Netherlands?
LikeLike
Hi Dirk,
No I’m suffering the same problems too. I’ve just sent them an email. This is the first time it’s not worked perfectly.
I’ve checked here
http://www.websitedown.info/vpnbook.com
and the site is down.
I did warn them that I’d release the blog in the US tomorrow (Sat) around 7 pm GMT… so they might be doing some maintenance.
Last Sunday 1,500 new customers connected. As a community project, I could be causing their servers some strain..
Let’s hope they’re just upgrading 🙂
LikeLike
Hi Dirk,
No, the Netherlands is VPNbook friendly. One of their DNS servers operates from the Netherlands, so this sounds more like a hiccup with VPNbook.
They have been offline for a day or so, due to maintenance, which they have completed.
They are a new, community project, so we do lose them now and again, as they upgrade the service. But they always come back, better than ever. 🙂
LikeLike
For some reason I can’t connect to vpnbook-udp53. I have no problem connecting vpnbook-tcp443. Could someone please help me? Anybody else facing the same problem?
LikeLike
Hi Jerry,
Could you right click on OpenVPN and instead of connect, select view log – and send me the error messages?
Thanks.
LikeLike
Hi Jerry,
I dread to ask this question, but have you got both certificates stored in c:\ program files\ OpenVPN \ config?
I know the answer is yes, as you sound an experienced VPN user, but would be my first thing to check, as each VPN provider, needs a separate certificate for each port (53 as well as 443). Clearly you have the certificate for port 443, as you’re connecting fine. But the certificate for port 53 might have become corrupted… so maybe download it a second time and see if it suddenly works for you.
LikeLike
My problem is that after i connect it stays connected for 6 sec and then reconnect ,, any help would be very nice… im on mac 10.8.2
LikeLike
Hi,
There’s maintenance happening at the moment on the UDP port 53 system. – so avoid that for a couple of days. 😦
VPNBook’s fastest TCP is port 81 – It’s much faster than TCP port 443, probably because it’s been introduced in the last couple of days. So if you use the port 81 – you’ll get higher speeds.
Hope that helpsl
LikeLike
I did try that also , same thing it going on connected for 6 sec than jumps off and reconnect and then the same thing is happening over again.:(
LikeLike
Can you copy and paste the errors for me.
When you right click on vpn – select view log instead of “connect” – and see what’s happening.
You’re using TCP Port 443 – is that right?
***
Hi, thanks for that.
I can see that
1. You’re on a Mac
2. You’re using port 81
3. The MTU errors are probably the cause of it.
There are 32 bytes difference…
2012-12-09 23:14:40 WARNING: ‘link-mtu’ is used inconsistently, local=’link-mtu 1592′, remote=’link-mtu 1560′ (Local link will try to send packets 1592, but the remote wants 1560 bytes..)
2012-12-09 23:14:40 WARNING: ‘tun-mtu’ is used inconsistently, local=’tun-mtu 1532′, remote=’tun-mtu 1500′
^^I’ve found a Mac based problem – that triggers the disconnection you were explaining..
I couldn’t work out how you were being disconnected but the forum link has been posted above for you.
LikeLike
This is from TCP 81 :
2012-12-09 23:14:22 *Tunnelblick: OS X 10.8.2; Tunnelblick 3.2.8 (build 2891.3099)
2012-12-09 23:14:22 *Tunnelblick: Attempting connection with vpnbook-TCP-81; Set nameserver = 1; monitoring connection
2012-12-09 23:14:22 *Tunnelblick: /Applications/Tunnelblick.app/Contents/Resources/openvpnstart start vpnbook-TCP-81.ovpn 1337 1 0 0 0 49 -atDASNGWrdasngw
2012-12-09 23:14:22 *Tunnelblick: openvpnstart: /Applications/Tunnelblick.app/Contents/Resources/openvpn/openvpn-2.2.1/openvpn –cd /Users/Amir/Library/Application Support/Tunnelblick/Configurations –daemon –management 127.0.0.1 1337 –config /Users/Amir/Library/Application Support/Tunnelblick/Configurations/vpnbook-TCP-81.ovpn –log /Library/Application Support/Tunnelblick/Logs/-SUsers-SAmir-SLibrary-SApplication Support-STunnelblick-SConfigurations-Svpnbook–TCP–81.ovpn.1_0_0_0_49.1337.openvpn.log –management-query-passwords –management-hold –script-security 2 –up /Applications/Tunnelblick.app/Contents/Resources/client.up.tunnelblick.sh -m -w -d -atDASNGWrdasngw –down /Applications/Tunnelblick.app/Contents/Resources/client.down.tunnelblick.sh -m -w -d -atDASNGWrdasngw –up-restart
2012-12-09 23:14:23 *Tunnelblick: openvpnstart message: Loading tun.kext
2012-12-09 23:14:23 OpenVPN 2.2.1 i386-apple-darwin10.8.0 [SSL] [LZO2] [PKCS11] [eurephia] built on Aug 10 2012
2012-12-09 23:14:23 MANAGEMENT: TCP Socket listening on 127.0.0.1:1337
2012-12-09 23:14:23 Need hold release from management interface, waiting…
2012-12-09 23:14:23 MANAGEMENT: Client connected from 127.0.0.1:1337
2012-12-09 23:14:23 MANAGEMENT: CMD ‘pid’
2012-12-09 23:14:23 MANAGEMENT: CMD ‘state on’
2012-12-09 23:14:23 MANAGEMENT: CMD ‘state’
2012-12-09 23:14:23 MANAGEMENT: CMD ‘hold release’
2012-12-09 23:14:23 *Tunnelblick: Established communication with OpenVPN
2012-12-09 23:14:23 *Tunnelblick: Obtained VPN username and password from the Keychain
2012-12-09 23:14:23 MANAGEMENT: CMD ‘username “Auth” “freeopenvpn”‘
2012-12-09 23:14:23 MANAGEMENT: CMD ‘password […]’
2012-12-09 23:14:23 WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
2012-12-09 23:14:23 NOTE: the current –script-security setting may allow this configuration to call user-defined scripts
2012-12-09 23:14:23 NOTE: –fast-io is disabled since we are not using UDP
2012-12-09 23:14:23 LZO compression initialized
2012-12-09 23:14:23 Control Channel MTU parms [ L:1592 D:140 EF:40 EB:0 ET:0 EL:0 ]
2012-12-09 23:14:23 Socket Buffers: R=[131072->65536] S=[131072->65536]
2012-12-09 23:14:23 Data Channel MTU parms [ L:1592 D:1450 EF:60 EB:135 ET:32 EL:0 AF:3/1 ]
2012-12-09 23:14:23 Local Options hash (VER=V4): ‘e4cf4bf0’
2012-12-09 23:14:23 Expected Remote Options hash (VER=V4): ‘b93029ce’
2012-12-09 23:14:23 Attempting to establish TCP connection with 195.60.76.223:81 [nonblock]
2012-12-09 23:14:23 MANAGEMENT: >STATE:1355091263,TCP_CONNECT,,,
2012-12-09 23:14:24 TCP connection established with 195.60.76.223:81
2012-12-09 23:14:24 TCPv4_CLIENT link local: [undef]
2012-12-09 23:14:24 TCPv4_CLIENT link remote: 195.60.76.223:81
2012-12-09 23:14:24 MANAGEMENT: >STATE:1355091264,WAIT,,,
2012-12-09 23:14:24 MANAGEMENT: >STATE:1355091264,AUTH,,,
2012-12-09 23:14:24 TLS: Initial packet from 195.60.76.223:81, sid=6d229950 b01e0c04
2012-12-09 23:14:24 WARNING: this configuration may cache passwords in memory — use the auth-nocache option to prevent this
2012-12-09 23:14:25 VERIFY OK: depth=1, /C=EU/ST=RO/L=Bucharest/O=VPNBook.com/OU=changeme/CN=ns.vpnbook.com/name=changeme/emailAddress=contact@vpnbook.com
2012-12-09 23:14:25 VERIFY OK: depth=0, /C=EU/ST=RO/L=Bucharest/O=VPNBook.com/OU=changeme/CN=ns.vpnbook.com/name=changeme/emailAddress=contact@vpnbook.com
2012-12-09 23:14:26 WARNING: ‘link-mtu’ is used inconsistently, local=’link-mtu 1592′, remote=’link-mtu 1560′
2012-12-09 23:14:26 WARNING: ‘tun-mtu’ is used inconsistently, local=’tun-mtu 1532′, remote=’tun-mtu 1500′
2012-12-09 23:14:26 Data Channel Encrypt: Cipher ‘AES-128-CBC’ initialized with 128 bit key
2012-12-09 23:14:26 Data Channel Encrypt: Using 160 bit message hash ‘SHA1’ for HMAC authentication
2012-12-09 23:14:26 Data Channel Decrypt: Cipher ‘AES-128-CBC’ initialized with 128 bit key
2012-12-09 23:14:26 Data Channel Decrypt: Using 160 bit message hash ‘SHA1’ for HMAC authentication
2012-12-09 23:14:26 Control Channel: TLSv1, cipher TLSv1/SSLv3 DHE-RSA-AES256-SHA, 1024 bit RSA
2012-12-09 23:14:26 [ns.vpnbook.com] Peer Connection Initiated with 195.60.76.223:81
2012-12-09 23:14:27 MANAGEMENT: >STATE:1355091267,GET_CONFIG,,,
2012-12-09 23:14:28 SENT CONTROL [ns.vpnbook.com]: ‘PUSH_REQUEST’ (status=1)
2012-12-09 23:14:28 PUSH: Received control message: ‘PUSH_REPLY,redirect-gateway def1,dhcp-option DNS 195.60.77.251,dhcp-option DNS 195.60.77.135,route 10.7.0.1,topology net30,ping 10,ping-restart 120,ifconfig 10.7.0.18 10.7.0.17’
2012-12-09 23:14:28 OPTIONS IMPORT: timers and/or timeouts modified
2012-12-09 23:14:28 OPTIONS IMPORT: –ifconfig/up options modified
2012-12-09 23:14:28 OPTIONS IMPORT: route options modified
2012-12-09 23:14:28 OPTIONS IMPORT: –ip-win32 and/or –dhcp-option options modified
2012-12-09 23:14:28 ROUTE default_gateway=192.168.1.1
2012-12-09 23:14:28 TUN/TAP device /dev/tun2 opened
2012-12-09 23:14:28 MANAGEMENT: >STATE:1355091268,ASSIGN_IP,,10.7.0.18,
2012-12-09 23:14:28 /sbin/ifconfig tun2 delete
ifconfig: ioctl (SIOCDIFADDR): Can’t assign requested address
2012-12-09 23:14:28 NOTE: Tried to delete pre-existing tun/tap instance — No Problem if failure
2012-12-09 23:14:28 /sbin/ifconfig tun2 10.7.0.18 10.7.0.17 mtu 1500 netmask 255.255.255.255 up
2012-12-09 23:14:28 /Applications/Tunnelblick.app/Contents/Resources/client.up.tunnelblick.sh -m -w -d -atDASNGWrdasngw tun2 1500 1592 10.7.0.18 10.7.0.17 init
No such key
2012-12-09 23:14:30 /sbin/route add -net 195.60.76.223 192.168.1.1 255.255.255.255
add net 195.60.76.223: gateway 192.168.1.1
2012-12-09 23:14:30 /sbin/route add -net 0.0.0.0 10.7.0.17 128.0.0.0
add net 0.0.0.0: gateway 10.7.0.17
2012-12-09 23:14:30 /sbin/route add -net 128.0.0.0 10.7.0.17 128.0.0.0
add net 128.0.0.0: gateway 10.7.0.17
2012-12-09 23:14:30 MANAGEMENT: >STATE:1355091270,ADD_ROUTES,,,
2012-12-09 23:14:30 /sbin/route add -net 10.7.0.1 10.7.0.17 255.255.255.255
add net 10.7.0.1: gateway 10.7.0.17
2012-12-09 23:14:30 Initialization Sequence Completed
2012-12-09 23:14:30 MANAGEMENT: >STATE:1355091270,CONNECTED,SUCCESS,10.7.0.18,195.60.76.223
2012-12-09 23:14:30 *Tunnelblick client.up.tunnelblick.sh: Unknown: ‘foreign_option_1’ = ‘dhcp-option DISABLE-NBT’
2012-12-09 23:14:30 *Tunnelblick client.up.tunnelblick.sh: Retrieved name server(s) [ 195.60.77.251 195.60.77.135 ] and WINS server(s) [ ] and using default domain name [ openvpn ]
2012-12-09 23:14:30 *Tunnelblick client.up.tunnelblick.sh: Up to two ‘No such key’ warnings are normal and may be ignored
2012-12-09 23:14:30 *Tunnelblick: Flushed the DNS cache
2012-12-09 23:14:30 *Tunnelblick client.up.tunnelblick.sh: Saved the DNS and WINS configurations for later use
2012-12-09 23:14:30 *Tunnelblick client.up.tunnelblick.sh: Set up to monitor system configuration with process-network-changes
2012-12-09 23:14:35 *Tunnelblick process-network-changes: SearchDomains changed from
*
* to
* {
* 0 : openvpn
* }
* pre-VPN was
*
2012-12-09 23:14:35 *Tunnelblick process-network-changes: SearchDomains changed; sending USR1 to OpenVPN (process ID 4269) to restart the connection.
2012-12-09 23:14:36 event_wait : Interrupted system call (code=4)
2012-12-09 23:14:36 TCP/UDP: Closing socket
2012-12-09 23:14:36 /Applications/Tunnelblick.app/Contents/Resources/client.down.tunnelblick.sh -m -w -d -atDASNGWrdasngw tun2 1500 1592 10.7.0.18 10.7.0.17 restart
2012-12-09 23:14:36 *Tunnelblick client.down.tunnelblick.sh: Cancelled monitoring of system configuration changes
2012-12-09 23:14:37 *Tunnelblick client.down.tunnelblick.sh: Restored the DNS and WINS configurations
2012-12-09 23:14:37 SIGUSR1[hard,] received, process restarting
2012-12-09 23:14:37 MANAGEMENT: >STATE:1355091277,RECONNECTING,SIGUSR1,,
2012-12-09 23:14:37 MANAGEMENT: CMD ‘hold release’
2012-12-09 23:14:37 WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
2012-12-09 23:14:37 NOTE: the current –script-security setting may allow this configuration to call user-defined scripts
2012-12-09 23:14:37 NOTE: –fast-io is disabled since we are not using UDP
2012-12-09 23:14:37 Re-using SSL/TLS context
2012-12-09 23:14:37 LZO compression initialized
2012-12-09 23:14:37 Control Channel MTU parms [ L:1592 D:140 EF:40 EB:0 ET:0 EL:0 ]
2012-12-09 23:14:37 Socket Buffers: R=[131072->65536] S=[131072->65536]
2012-12-09 23:14:37 Data Channel MTU parms [ L:1592 D:1450 EF:60 EB:135 ET:32 EL:0 AF:3/1 ]
2012-12-09 23:14:37 Local Options hash (VER=V4): ‘e4cf4bf0’
2012-12-09 23:14:37 Expected Remote Options hash (VER=V4): ‘b93029ce’
2012-12-09 23:14:37 Attempting to establish TCP connection with 195.60.76.223:81 [nonblock]
2012-12-09 23:14:37 MANAGEMENT: >STATE:1355091277,TCP_CONNECT,,,
2012-12-09 23:14:38 TCP connection established with 195.60.76.223:81
2012-12-09 23:14:38 TCPv4_CLIENT link local: [undef]
2012-12-09 23:14:38 TCPv4_CLIENT link remote: 195.60.76.223:81
2012-12-09 23:14:38 MANAGEMENT: >STATE:1355091278,WAIT,,,
2012-12-09 23:14:38 MANAGEMENT: >STATE:1355091278,AUTH,,,
2012-12-09 23:14:38 TLS: Initial packet from 195.60.76.223:81, sid=f9a4bb02 4e4ba5d0
2012-12-09 23:14:39 VERIFY OK: depth=1, /C=EU/ST=RO/L=Bucharest/O=VPNBook.com/OU=changeme/CN=ns.vpnbook.com/name=changeme/emailAddress=contact@vpnbook.com
2012-12-09 23:14:39 VERIFY OK: depth=0, /C=EU/ST=RO/L=Bucharest/O=VPNBook.com/OU=changeme/CN=ns.vpnbook.com/name=changeme/emailAddress=contact@vpnbook.com
2012-12-09 23:14:40 WARNING: ‘link-mtu’ is used inconsistently, local=’link-mtu 1592′, remote=’link-mtu 1560′
2012-12-09 23:14:40 WARNING: ‘tun-mtu’ is used inconsistently, local=’tun-mtu 1532′, remote=’tun-mtu 1500′
2012-12-09 23:14:40 Data Channel Encrypt: Cipher ‘AES-128-CBC’ initialized with 128 bit key
2012-12-09 23:14:40 Data Channel Encrypt: Using 160 bit message hash ‘SHA1’ for HMAC authentication
2012-12-09 23:14:40 Data Channel Decrypt: Cipher ‘AES-128-CBC’ initialized with 128 bit key
2012-12-09 23:14:40 Data Channel Decrypt: Using 160 bit message hash ‘SHA1’ for HMAC authentication
2012-12-09 23:14:40 Control Channel: TLSv1, cipher TLSv1/SSLv3 DHE-RSA-AES256-SHA, 1024 bit RSA
2012-12-09 23:14:40 [ns.vpnbook.com] Peer Connection Initiated with 195.60.76.223:81
2012-12-09 23:14:41 MANAGEMENT: >STATE:1355091281,GET_CONFIG,,,
2012-12-09 23:14:42 SENT CONTROL [ns.vpnbook.com]: ‘PUSH_REQUEST’ (status=1)
2012-12-09 23:14:42 PUSH: Received control message: ‘PUSH_REPLY,redirect-gateway def1,dhcp-option DNS 195.60.77.251,dhcp-option DNS 195.60.77.135,route 10.7.0.1,topology net30,ping 10,ping-restart 120,ifconfig 10.7.0.18 10.7.0.17’
2012-12-09 23:14:42 OPTIONS IMPORT: timers and/or timeouts modified
2012-12-09 23:14:42 OPTIONS IMPORT: –ifconfig/up options modified
2012-12-09 23:14:42 OPTIONS IMPORT: route options modified
2012-12-09 23:14:42 OPTIONS IMPORT: –ip-win32 and/or –dhcp-option options modified
2012-12-09 23:14:42 Preserving previous TUN/TAP instance: tun2
2012-12-09 23:14:42 /Applications/Tunnelblick.app/Contents/Resources/client.up.tunnelblick.sh -m -w -d -atDASNGWrdasngw tun2 1500 1592 10.7.0.18 10.7.0.17 restart
No such key
2012-12-09 23:14:44 *Tunnelblick client.up.tunnelblick.sh: Unknown: ‘foreign_option_1’ = ‘dhcp-option DISABLE-NBT’
2012-12-09 23:14:44 *Tunnelblick client.up.tunnelblick.sh: Retrieved name server(s) [ 195.60.77.251 195.60.77.135 ] and WINS server(s) [ ] and using default domain name [ openvpn ]
2012-12-09 23:14:44 *Tunnelblick client.up.tunnelblick.sh: Up to two ‘No such key’ warnings are normal and may be ignored
2012-12-09 23:14:44 *Tunnelblick: Flushed the DNS cache
2012-12-09 23:14:44 *Tunnelblick client.up.tunnelblick.sh: Saved the DNS and WINS configurations for later use
2012-12-09 23:14:44 *Tunnelblick client.up.tunnelblick.sh: Set up to monitor system configuration with process-network-changes
LikeLike
I’ve been on the forum for TunnelBlick – and found this problem – which is what I think you’re telling me is happening…
https://code.google.com/p/tunnelblick/issues/detail?id=206
On OS X 10.8.1 or 10.8.2 (“Mountain Lion”) some configurations that use “Set nameserver” causes Tunnelblick to continuously disconnect and reconnect the configuration.
The disconnect/reconnect will appear in the log as something similar to:
2012-03-26 22:17:33 *Tunnelblick process-network-changes: SearchDomains changed from
*
* to
* {
* 0 : openvpn
* }
* pre-VPN was
*
There’s a full discussion on there… I’m pretty sure this is what’s happening.
LikeLike
Thanks a lot for helping me out finally i got an answer .. it has worked before but the last week or so i gets these errors / drops.. again thanks for looking into this! much appreciated!
LikeLike
No problem, thanks for asking a great question.
I’m learning so much, that it’s a pleasure. 🙂
LikeLike
i am using udp port 25000 and since last couple days , the vpn first gets disconnected after opening websites and then never connects unless restarted and then again the same process follows . 😦 …..i am using windows 7… plz help
LikeLike
Just checked the VPNbook site in case they’ve reissued new certificates.
They are commenting that
If you are having connection/disconnection issues, make sure you are using the Latest “OpenVPN Client 2.3_rc2” released on 2012.12.18
Are you running the new OpenVPN client?
LikeLike
VPNBook upgraded the OpenVPN client. Have you downloaded the new client?
I’ve written a guide for this, hope this helps. 🙂
LikeLike
followed ur advice … downloaded the new set up 2.3.0 version and the new udp 25000 certificate but still the same problem exists. the blue icon turns to yellow after few seconds … 😦 .. plz help
LikeLike
Hiya,
Just connected to UDP port 25000 and she’s bouncing like like a kangeroo at the moment. Therefore this is a Server issue, not local to you, so we have to wait for VPNBook to fix it. 😦
If you look at the log of the connection, you’ll see
Tue Jan 08 17:23:00 2013 FRAG_IN error flags=0xfa2a187b: FRAG_TEST not implemented
Tue Jan 08 17:23:05 2013 FRAG_IN error flags=0xfa2a187b: FRAG_TEST not implemented
Tue Jan 08 17:23:10 2013 FRAG_IN error flags=0xfa2a187b: FRAG_TEST not implemented
Tue Jan 08 17:23:16 2013 FRAG_IN error flags=0xfa2a187b: FRAG_TEST not implemented
But there’s nothing we can do at the moment, this has to be a VPNBook fix.
LikeLike
Hiya,
I’m currently on TCP port 80 – VPNBook.
So you can work using TCP port 80 instead of UDP port 25000?
That way, you’ll get a stable connection.
And they’ll have time to work on Port 25000.
Take care. 🙂
LikeLike
I can’t connect. I keep getting an auth failure.
LikeLike
Any chance of getting me an error message.
Also are you connecting via tcp say port 80 or udp say port 53?
As I’ll go test that port’s connectivity.
It could be that one port is overwhelmed, but the others are working fine. I’ll go check that out for you.
LikeLike
im trying to set up vpnbook on my tomato router but i cant seem to find any “how to” sites that help….ive been able to open the config file in notebook and i can see the ip and port settings as well as the tap/tun etc and i can set that up but when it comes time to enter the keys it asks for 3 different keys: certificate authority, client certificate, and the client key…im new to VPNs and it gets very frustrating when i find ppl commenting on how well it works in tomato but i cant find out how they get it to work….any help?
LikeLiked by 1 person
Hi Shane,
Great question.
Here’s the hidemyass guide to PPTP on the tomato router – you could definitely start here
http://wiki.hidemyass.com/Tomato_PPTP_Setup
HOw to GEEK guide to OpenVPN (on your router, without VPNBOOK).
http://www.howtogeek.com/60774/connect-to-your-home-network-from-anywhere-with-openvpn-and-tomato/
My dastardly plan, is that if you can successfully install openvpn onto the tomato router, then 90% of the work is done.
You’ll have generated your private keys etc.
This is probably how your friends are using it – they are using the router as a server.
As the server is under your control, you can generate the keys.
I can see that hide my ass offer the 3 keys you mention…
http://wiki.hidemyass.com/Tomato_OpenVPN_Setup
Scroll down – as you’d never beleive there was a good visual guide hidden at the bottom.
the certificate authority.
download the vpnbook.crt – open it up. Under general tab – TRUST CERTIFICATE button (at the bottom of the page).
When you download the winzip from VPNBOOK, you’ll get the .crt files.
The PPTP on vpnbook looks the easiest to start off with. There’s no reason that shouldn’t work for you.
Likewise using the tomato router with openvpn would also work.
By the way I don’t use hidemyass, so I’m not recommending them. It’s just that they do have a guide for your router.
LikeLiked by 1 person
Hi Shane,
I’ve checked with a paid for VPN, and I get a .CA file.
But I don’t appear to have one for VPNBook. So PPTP seems to be the way to go, so that you can use the tomato router, and free Vpnbook.
The other alternative, is that you pay for a VPN, and then you’ll get the .CA files.
Hope that helps.
LikeLike
thank you for your reply…..i had found tutorials for hma and openvpn all over the place and they all seem to be slightly different in the setup process and i had muddled through using them untill i ran into the “entering keys” problem where it seems vpnbook is missing one of the keys as you had said…im looking for something more secure than pptp and i know openvpn will work on my router which is an asus rt-n16 with tomato usb installed on it…if i can get it to work all my internet devices will be protected through the same vpn service including my skype phone
thank you for your help, you have pointed out a few things that i had missed in my searches
LikeLike
Hiya,
No problem – it’s an interesting question. The router seems to be able to use OpenVPN in 2 different ways, so it looks like it’s worth an experiment.
PPTP is dodgy in comparision to OpenVPN, so I accept your point there, totally. OpenVPN was designed to sidestep Chinese and Russian state surveillance, so it’s the bulletproof software. 🙂
Interesting connection for you regarding Skype.
M$ invented a node interception technology… and then 2 weeks later bought Skype. Yes, I might be adding up 2+2 and getting 5, but m$ might be getting heavily into interception and surveillance technology as a money spinner, so be warned regarding Skype.
LikeLike
If you open the vpnbook.crt
go to the details tab
show all
authority field indentifier = whole bunch of keys are show.
COPY to FILE
Export certificate wizard will run
you’d need to call this file CA (it’ll add .crt) as the ending for you.
This may generate a .CA for VPNBOOK.
Worth a shot. 🙂
Great question…
LikeLike
there is also a tab in tomato for the client version as well as the server…..so it is possible to set the router up as the client
LikeLike
Definitely give the client tab a go. You have the client config files from vpnbook.
If you use winzip open up the vpnbook.crt file (it’s the security certificate).
GENERAL TAB – Install Certificate
SHOW = Version 1 fields only
PUBLIC KEY = RSA 1024 bit – Last option
Then the keys will be displayed.
We might be able just to use copy and paste for these… to put them into your tomato router.
COPY to file button
This triggers the EXPORT CERTIFICATE WIZARD to run for you.
NEXT button
Format?? No idea what you’d need to use here, it defaults to DER X509…
What format would your tomato router want?
Differences – from their help file
Personal Information Exchange (PKCS #12)
the Personal Information Exchange format (PFX, also called PKCS #12) supports secure storage of certificates, private keys, and all certificates in a certification path.
The PKCS #12 format is the only file format that can be used to export a certificate and its private key.
Cryptographic Message Syntax Standard (PKCS #7)
The PKCS #7 format supports storage of certificates and all certificates in the certification path.
DER-encoded binary X.509
The Distinguished Encoding Rules (DER) format supports storage of a single certificate. This format does not support storage of the private key or certification path.
Base64-encoded X.509
The Base64 format supports storage of a single certificate. This format does not support storage of the private key or certification path.
NEXT Button
err file name… dunno. See if we can copy and paste instead. 🙂
I can find good visual instructions to the WRT Router
https://www.goldenfrog.com/support/vyprvpn/dd-wrt-router-openvpn
This is what make me think that copy and paste is the easiest way to transfer the keys.
Supported Routers
Asus – Rt-N56U
Cisco Linksys – E3000, E3200, E4200, E4500
D-Link – DIR-632, DIR-825
Netgear – WNR3500, WNDR3700
LikeLike
***OPENVPN BLOG*** Found out our problem.
http://openvpn.net/index.php/access-server/docs/admin-guides/228-how-to-extract-the-ca-cert-and-key-from-openvpn-as-certificates.html
How to extract the CA, CERT, and KEY from OpenVPN-AS Certificates
Some UTM’s and VOIP systems require a user to supply a CA, CERT and KEY, since we have bundled all of these into one file you will need to run the following commands to extract them:
We package the certs/keys along with the client config to reduce the configuration to one file. However, using the CLI Get5 method, it is possible to get a configuration with separated files:
By default OpenVPN assumes you are using Public Key Infrastructure (PKI) for Authentication (the SSL/TLS Client option in Viscosity). For this to work OpenVPN expects you to define a CA certificate, a client certificate, and a client key (or a pkcs12 file that combines all of these). If these are not defined then you will receive the error message you are getting.
These files should have been supplied to you by your VPN provider.
LikeLike
I’m getting connecting to UDP-53 failed. What is it that I’m doing wrong?
What is it that I’m doing wrong?
thanks for any help you may offer.
Sun Mar 24 02:55:49 2013 OpenVPN 2.3.0 x86_64-w64-mingw32 [SSL (OpenSSL)] [LZO] [PKCS11] [eurephia] [IPv6] built on Mar 7 2013
Enter Management Password:
Sun Mar 24 02:55:49 2013 MANAGEMENT: TCP Socket listening on [AF_INET]127.0.0.1:25340
Sun Mar 24 02:55:49 2013 Need hold release from management interface, waiting…
Sun Mar 24 02:55:49 2013 MANAGEMENT: Client connected from [AF_INET]127.0.0.1:25340
Sun Mar 24 02:55:49 2013 MANAGEMENT: CMD ‘state on’
Sun Mar 24 02:55:49 2013 MANAGEMENT: CMD ‘log all on’
Sun Mar 24 02:55:49 2013 MANAGEMENT: CMD ‘hold off’
Sun Mar 24 02:55:49 2013 MANAGEMENT: CMD ‘hold release’
Sun Mar 24 02:56:01 2013 MANAGEMENT: CMD ‘username “Auth” “freeopenvpn”‘
Sun Mar 24 02:56:01 2013 MANAGEMENT: CMD ‘password […]’
Sun Mar 24 02:56:01 2013 WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
Sun Mar 24 02:56:01 2013 NOTE: OpenVPN 2.1 requires ‘–script-security 2’ or higher to call user-defined scripts or executables
Sun Mar 24 02:56:01 2013 NOTE: –fast-io is disabled since we are running on Windows
Sun Mar 24 02:56:01 2013 Socket Buffers: R=[8192->8192] S=[8192->8192]
Sun Mar 24 02:56:01 2013 UDPv4 link local: [undef]
Sun Mar 24 02:56:01 2013 UDPv4 link remote: [AF_INET]93.114.44.253:53
Sun Mar 24 02:56:01 2013 MANAGEMENT: >STATE:1364057761,WAIT,,,
Sun Mar 24 02:56:03 2013 read UDPv4: Connection reset by peer (WSAECONNRESET) (code=10054)
Sun Mar 24 02:56:04 2013 read UDPv4: Connection reset by peer (WSAECONNRESET) (code=10054)
Sun Mar 24 02:56:08 2013 read UDPv4: Connection reset by peer (WSAECONNRESET) (code=10054)
Sun Mar 24 02:56:18 2013 read UDPv4: Connection reset by peer (WSAECONNRESET) (code=10054)
Sun Mar 24 02:56:34 2013 SIGTERM[hard,] received, process exiting
Sun Mar 24 02:56:34 2013 MANAGEMENT: >STATE:1364057794,EXITING,SIGTERM,,
LikeLike
Hi Ace,
I’ve found someone else with this error. It seems to be a hiccup with the certificates.
If you can have a go at re copying all the Vpnbook certs and configs to
c: > all programs > openvpn > config.
and then see if udp port 53 works.
http://forums.contribs.org/index.php?topic=45612.0
LikeLike
vpn is not connecting anymore this is what it says
SENT CONTROL [ns.vpnbook.com]: ‘PUSH_REQUEST’ (status=1)
AUTH: Received control message: AUTH_FAILED
SIGUSR1[soft,auth-failure] received, process restarting
MANAGEMENT: >STATE:1366781533,RECONNECTING,auth-failure,,
plz suggest what to do ??
LikeLike
Hi Ron,
Authorisation failure – so you need to check which password you’re using.
VPNBook changed their passwords earlier.. they do from time to time.
Currently this is on their site..
Apr 21, 2013 – Username and Password Changed. Check Below for New Login
Server #1: euro1.vpnbook.com
Server #2: euro2.vpnbook.com
Username: vpnbook
Password: wUvr8kjM
LikeLike
Hi
I changed the password now this comes up
MANAGEMENT: Client disconnected
There are no TAP-Windows adapters on this system. You should be able to create a TAP-Windows adapter by going to Start -> All Programs -> OpenVPN -> Add a new TAP-Windows virtual ethernet adapter.
and then
“Connecting to vpnbook-UDP25000 has failed ”
please suggest
LikeLike
Hi Ron,
You could try removing OpenVPN and reinstalling it – or this.
Error: There are no TAP32 adapters on this system
You are be able to create a TAP-Win32 adapter by going to: START -> ALL PROGRAMS -> OPENVPN -> UTILITIES -> ADD A NEW TAP VIRTUAL ETHERNET ADAPTER (and make sure to run the script as admin).
(To be admin, right click on OpenVPN and select RUN AS ADMIN).
SURFBouncer has good graphics
http://www.surfbouncer.com/TAP_adapter.htm
Follow this through, and it shows you exactly what to do. 🙂
Offical OpenVPN advice was (without graphics).
If you want to run multiple OpenVPN instances on the same machine, each using a different configuration file, it is possible if you:
Use a different port number for each instance (the UDP and TCP protocols use different port spaces so you can run one daemon listening on UDP-1194 and another on TCP-1194).
If you are using Windows, each OpenVPN configuration needs to have its own TAP-Windows adapter. You can add additional adapters by going to Start Menu -> All Programs -> TAP-Windows -> Add a new TAP-Windows virtual ethernet adapter.
http://openvpn.net/index.php/open-source/documentation/howto.html
It seems to be a common hiccup. Let me know how you get on.:)
LikeLike
hey .. thanks .. it worked this time !!!!!
LikeLike
Hi Ron,
Brilliant! Always glad to get another protected with VPN’s 🙂
LikeLike
Hi
this is the problem i am facing for last couple of days …
NOTE: –fast-io is disabled since we are running on Windows
Thu May 02 20:22:10 2013 Socket Buffers: R=[8192->8192] S=[8192->8192]
Thu May 02 20:22:10 2013 UDPv4 link local: [undef]
Thu May 02 20:22:10 2013 UDPv4 link remote: [AF_INET]93.114.44.253:25000
Thu May 02 20:22:10 2013 MANAGEMENT: >STATE:1367551330,WAIT,,,
after wait it reconnects and stays that way .. plz help !!!
LikeLike
Hello !!!!!…Can anyone fix the problem plz !!!!!
LikeLike
is this vpn service still working
LikeLike
Hi Eric,
Checkout http://www.vpnbook.com/ for their latest passwords.
These change every month.
The sites states that all VPN’s are online.
If you have any issues,the website will report if a service is down for the UK or Netherlands or US.
Hope that helps.
LikeLike
Please tell me which to choose UDP 25, TCP 443,TCP 80 AND UDP 25000
LikeLike
Hi John,
UDP is faster but less stable. It’s called “connectionless”, so there’s no resending of lost data.
TCP is slower, but more reliable. TCP resend lost data – but that checking slows it down.
Hope that helps.
LikeLike
Please tell me which one is more reliable secure and fast thanks
LikeLike
Hi John,
The most reliable protocol is TCP – as it numbers the packets and checks that they’ve arrived.
If they don’t arrive TCP will resend lost packets…
LikeLike
Sorry I write UDP 25 instead of UDP 53
LikeLike
During Setup in Step-1 you said to download the Certificate for TCP Port 80, but in Step-2 you unzip the UDP 53 as is shown in picture. So which one to choose?
LikeLike
Hi John,
If you want a reliable connection, select TCP port 80.
If you want a faster connection, but a less stable one, use UDP port 53.
LikeLike
Hi All,,
For 2-3 weeks i m both connecting with pptp and vpn client without any problem.But non of forbidden pages are opening any more,says still blocked?Whats the problem here? Thanks
LikeLike