OAuth 2 – the 4 Grant types
OAuth2 has 4 grant types. Each grant has a different sequence of steps. Clearly each grant is designed for a different situation.
This is why Oauth flows confuse people. The steps and sequence will be different for each flow.
Visual Guide to Flows
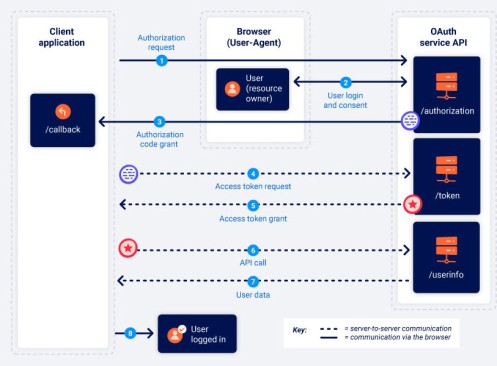
The diagram below is the best visual guide to OAuth, that I’ve come across in several years.
The client, makes an authorisation request (via a browser).
The /authorization end point of the OAuth server, deals with the user login and consent.
Next, the /authorization endpoint sends a code out, to the /callback endpoint of the client.
The /callback is detailed in the redirect_uri parameter.
An example would be:
GET /callback?code=a1b2c3d4e5f6g7h8&state=ae13d489bd00e3c24 HTTP/1.1 Host: client-app.com
Now communication via the browser stops – and the sequence continues in secret, as server to server communication
The Client has a CODE… but the code needs to be exchanged for a TOKEN.
This is what happens in the exchange of CODE for a TOKEN (called an ACCESS TOKEN REQUEST) – Step 4.
It makes a POST call to the /token endpoint, to make the exchange.
An example would be:
POST /token HTTP/1.1 Host: oauth-authorization-server.com … client_id=12345&client_secret=SECRET&redirect_uri=https://client-app.com/callback&grant_type=authorization_code&code=a1b2c3d4e5f6g7h8
The /token endpoint of the OAuth server sends token request back to the client – called an ACCESS TOKEN GRANT – Step 5.
An example would be:
{ “access_token”: “z0y9x8w7v6u5”, “token_type”: “Bearer”, “expires_in”: 3600, “scope”: “openid profile”, … }
The Access token grant is FROM to the /token endpoint of the Oauth Server to the client.
Now all transactions moves to a different endpoint.
An API call is made by the client, to the /userinfo endpont of the OAuth server. The Access Token is sent to the /userinfo endpoint, as evidence, it is allowed access.
An example would be:
GET /userinfo HTTP/1.1 Host: oauth-resource-server.com Authorization: Bearer z0y9x8w7v6u5
The final step is that user data is returned from /userinfo endpoint, of the OAuth server to the Client, so that the user can be logged in.
- Code Flow
The code flow is the most secure.
Used where the client can keep secrets.
Code is between the Auth Server and the Resource Server.

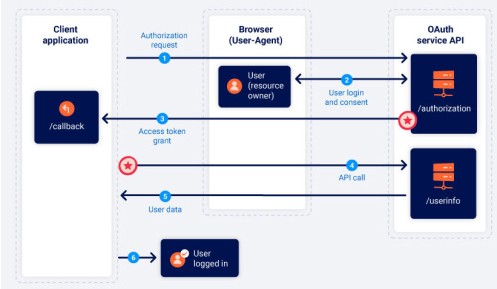
2. Implicit Flow
Immediate Token is sent. No code is sent. Gives immediate access. Used where a client cannot keep a secret, so no point in sending a code, eg a mobile.
PUBLIC CLIENT, as in mobile or web browser.
3. Resource Owner
You enter your facebook password into the facebook app on your phone.
You trust the mobile app with your password, as they own the app, a breach isn’t in their interests.
4. Client Credentials
Used for the client to access its own resources, or information about itself.
Reference: